Why we choose a WiFi conference system and how to select it?
How do I make sure the wireless system works?
Today, a lot of digital wireless equipment works in the licence-free 2.4GHz band. Most commonly known is Wireless LAN. At first glance, you might think that if you have a wireless conferencing system that works in this popular band you are as snug as a bug in a rug. Wrong. The reality is quite the opposite. The 2.4GHz wireless band offers room for only three non-overlapping wireless systems. Non-overlapping means that they are not interfering with one another. Each system therefore eats one third of the available bandwidth. So having two Wireless LAN networks in the vicinity significantly reduces the possibility of running a conference system reliably. Increasing the transmission power of the conference system to blast away the competition from Wireless LAN is a very crude way of resolving this and might result in unhappy delegates who can’t use their wireless laptop connection during the meeting. It is not the solution either if you have several conference systems operational in adjacent rooms. The solution is a multi-band wireless conference system that also works in the licence-free 5GHz band. This will give you a multitude of channels to work in and allows you to stay out of the very busy 2.4GHz band. Moreover, it will make your IT department more relaxed if it knows that your system is not messing with the Wireless LAN in your building.
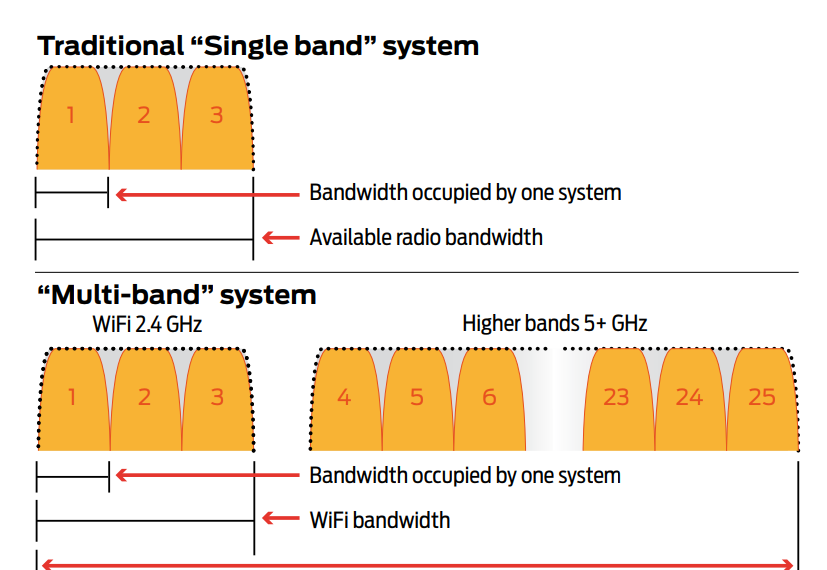
Can I run multiple systems in one building or on the same floor?
With a multi-band wireless system that works in the 2.4GHz and 5GHz bands, you have 25 channels to choose from (in Europe). So you can set each system up to work on a different channel, so that one doesn’t interfere with the other. In theory – if each channel is available – you can run 25 completely separate systems in one building.
How do I know which frequencies are free in my building?
The answer to this is fairly straightforward: make sure that your wireless conference system has a built-in spectrum analyser that constantly monitors the available spectrum and visualises the activity on a web page. It will allow you to do two things. If you wish to keep control of the frequencies that your system is using, you can easily see which channels are free. With a simple mouse click you can then select the channel in which you want your system to operate. However, spectral conditions can change and channels that are available today might be taken by other systems tomorrow. To keep your system operational in such volatile situations, you can set up your system to automatically and unnoticeably change to a free channel. In this mode, the system guarantees maximum audio quality and reliable operation.
Are these systems complex to set up?
On the contrary, a wireless conferencing system in its most basic form – that is, audio only – is extremely easy to set up. The only components in the system are the Delegate Units and a Wireless Access Point. In this case, you don’t need the central unit. Bring in your laptop, or connect the access point to the local area network to set up the system with the intuitive web pages provided, and you’re good to go. Can I easily connect other audio equipment? The wireless access point has an analogue audio input as well as an output. Connecting a wired or wireless microphone, a video-conferencing system or an audio recorder is just a matter of connecting a cable. So with a minimum amount of equipment, you have a fully operational system. What if I also need voting and language distribution? Today, wireless conferencing systems exist in a multitude of flavours, offering three- or five-button voting as well as RF language distribution. The latter eliminates the need to add an infrared language distribution system and again reduces the complexity of the installation. State-of-the art wireless RF conference systems go as far as offering at least 40 language channels, surpassing the capabilities of current IR systems.
How do I make sure that batteries don’t run out during a meeting?
Obviously, with wireless units running on batteries, there are some simple rules of thumb to keep in mind when setting up a meeting. First of all, make sure that your batteries can last the duration of the meeting – and take into account the possibility of the meeting overrunning. With the web interface you can easily check the condition of the battery of each unit and see the number of hours remaining. You can even check this during the meeting, without anybody noticing. Should you discover that one of the batteries is running out, you can wait for the coffee break to exchange it for a new one, or connect a wall plug adapter to the battery so it continues working and charges at the same time. How do I keep my batteries in good condition? This really depends on the battery technology. If you have nickel-metal hydride (NiMH) batteries, you will need to discharge them fully before you recharge to avoid loss of battery autonomy over time, due to the memory effect. Better is to use lithium-ion (Li-Ion) batteries. This battery technology does not require a discharge-before-charge cycle. This significantly reduces the time needed to keep your batteries in good shape and there is no loss of autonomy due to memory effect.
How Can I guarantee the confidentiality of the meeting?
It goes without saying that security is an important issue and should not be treated lightly. But consider this: if you make the right choice, anyone trying to listen in on your meeting would have to leap three major hurdles. The first is proprietary protocol. Make sure that your system uses a communication protocol that is proprietary to the manufacturer of the gear. If the eavesdropper does not have the same type of equipment, he will have to figure out first how the communication protocol works before he can start decoding information. It would be like putting a 1,000-piece jigsaw puzzle together with no image on the pieces. Then there is the access list – a list of identified and trusted units that are part of your conference system. This access list is stored in the system and used to verify whether a unit is allowed to be part of the system. A rogue unit that tries to connect will be rejected because its unique identifier is not in the list of trusted units. Finally, encryption. If your system supports this, all communication between the delegate units and the Wireless Conference Access point will be secured with an encryption key. Be sure though to select a system that uses an encryption key of at least 128 bits. With these security measures in place, unauthorized eavesdropping is virtually impossible. Multi-band systems give users in Europe 25 channels to choose from, preventing interference from other wireless technologies.












